As a continuation to part 1, I have some really good news, my goal for this task has been achieved. We now have a fully functional Nagios server, which is providing ongoing network monitoring for a client on a separate machine.
In an effort to offer a high level insight into the approach I took, with the assigned task of setting up a client machine to be monitored by dedicated host (Nagios Server) on another machine. The initial stages of setting up a Nagios client on another machine involved the creation of a user (named nagios) and the assignment of password for that user. Then I had to obtain NRPE (Nagios Remote Plug-in Executor) plugins for both machines. The tarball files were obtained via a dedicated Nagios software web source. Once those files were downloaded and extracted onto the respective machines (Client and Server), I then proceeded to fulfill the compile and install process. As with every build however, there are always bumps in the road. One of the bumps I encountered occured during of compiliing the NRPE plugin. The error that I was faced with prompted me to do some additional research, as the tutorial that used did not highlight or integrate the needed actions to circumvent such a problem. See screenshot which helps to reflect this occurence.
During my research I came across a website that offered relevant info to resolving this issue: Assistive Resource Link -> Under the Section compile and configure NRPE it says that "you need the openssl-devel package installed to compile NRPE with SSL support." So issued the yum install (yum utility) to add the needed library, and tried recompiling; as a result the compile and install process proved to be successful.
I then had to install the the plug-ins for "in-house" testing, followed by the installation of the NRPE daemon as a service, using the command make install-xinetd. The next step involved modifying the NRPE configuration file -> /etc/xinetd.d/nrpe, here I added the IP address of the host machine (server).
I then had to change the firewall settings on the client machine, so thereby allowing the host to connect to client, without firewall interruption.
For the firewall settings I used the command --> iptables -I INPUT -p tcp -m tcp ---dport 5666 -j ACCEPT which provided access to the Registered port number 5666 on the client. (The configuration on the client is complete)
I then had to compile and install the NRPE tarball addon to the host machine, and also create and make some changes to one of two relevant config files located in --> /usr/local/nagios/etc/command.cfg -> /usr/local/nagios/etc/objects/command.cfg
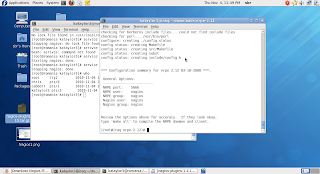
The next phase involved "Adding services to be monitored on the remote system." To succcessfully achieve that objective I was required to create template from 'scratch' which is formatted as a mirror of actual example template file that comes with NRPE by default. Within the newly created template file, I created a number of host and service definitions, and then ran a "Pre-flight" run to check for possible errors in the confiiguration files --Pre-flight command syntax: /usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfg
Once the test produces zero errors then the process is 99.9% completed. Next the firewall on the host machine needs to be modified to allow outgoing traffic to the client on the respective port address. The xinetd service needs to be restarted on the client and the nagios service needs to be restarted on the host considering changes were made to the config files on both systems. Success!!!!
Next up! Phase 2 implementation of Nagios on other machines, details will be released as time progresses...its sleep time....
Link to install documentation: http://nagios.sourceforge.net/docs/nrpe/NRPE.pdf
Subscribe to:
Post Comments (Atom)



No comments:
Post a Comment